
How many times do you think that you are photographed a day? Statistics show that people in the metropolitan areas are subjected to filming 83 times a day on average, and when walking down the street, it is equivalent to the rate of once per nine seconds. Notably, most of these images are taken by surveillance cameras for safety purposes, or CCTVs. Take one step out of your home, and you will be surrounded by a successive series of CCTVs present everywhere, as in the elevator, public transportation, road, markets, and convenience stores. At an early stage, some expressed inconvenience and discomfort about being unwillingly photographed, but CCTVs have now become part of our lives.
01
How CCTV Images Have Been Managed So Far

First of all, what is a CCTV system, or a surveillance camera? The word “CCTV” is an acronym for Closed-circuit Television, and the system is a combination of cameras directly connected to recording devices. It is also known as the closed-circuit system because its images are not made available to external users. In the past, image recording was conducted using videotapes, and thus users had the bother of changing videotapes every day and had difficulty storing recorded videotapes for a long time.
To address these limitations, Digital Video Recorder (DVR) systems—devices equipped with hard disk drives to store images—have taken over for videotape-based systems. The application of DVR allows users to store images acquired from dozens of CCTVs on hard disk drives and manage them according to the date on and place at which they were created. It has taken a long time, however, for DVR to be connected to the Internet network because such connection has been prohibited for security applications in apartment complexes and other buildings. Also, recorded images are not something that everyone can have access to, even when they visit the security office and make requests. Images of children playing at playgrounds were occasionally made available to their parents, but granting any sort of further access requires that clear grounds be presented or permission from the Police. Considering that reckless disclosure of such images might lead to trouble, e.g., an invasion of privacy, the dissemination of CCTV images through the Internet has not been allowed, and only administrators have been given access to those data.
In the meantime, a group of residents from an apartment complex filed a complaint against the government arguing that it permit connecting their CCTVs to the Internet so that these cameras can function as network cameras. In response, the government accepted the argument based on its judgment that there would no longer be a need to regulate the use of CCTV image data. After having continuously developed and evolved, where will this CCTV technology be headed in the future?
02
CCTVs Capable of Warning against Danger in Advance
Network cameras and CCTVs are basically the same in terms of basic function. Network cameras, however, vary from CCTV in that users can have external access through the Internet to recorded images. The act of transmitting images to external entities can be interpreted in two ways. The first meaning is that users outside the building can watch transmitted images through streaming technology. The second meaning is that cloud computing is made possible and available, allowing the management of image data.
Cloud computing is a computing environment in which users, using the Internet, store data on virtual servers; when necessary, computing is implemented through IT devices, such as desktop computers, personal computers, laptops, and smartphones. For that reason, another name for a network camera is a Cloud Cam.
The use of network cameras allows users to upload image data to the cloud system, thereby reducing costs compared to when DVR devices are applied and also making it easier for administrators to quickly access images taken with smartphones.
With these many advantages of network cameras, public expectations are rising. Indeed, the most pronounced trend in AI and data analysis fields has been the focus on image information. Today, AI technology is capable of identifying objects in camera images and further understanding the context of what is happening in those images. Network cameras, when combined with advanced image analysis technology, will significantly enhance the utility and convenience of CCTVs.
At its 2007 conference, Microsoft presented the case of applying AI and surveillance camera technology to industrial sites. Its cloud computing-based AI recognizes human faces and thus informs administrators of visits of outsiders who are not registered to the specific site. Also, the AI is capable of detecting dangerous objects that have not been properly placed or stored, such as electric saws lying idle, and sending signals to administrators. So far, surveillance cameras have mainly been used to track back to what has already happened, as reactive responses, but the technology can now serve as an effective tool to proactively manage and prevent dangerous situations.
In this way, AI-based image analysis technology is continuing to advance and evolve. ETRI is also engaged in the development of CCTV for security purposes, combined with AI technology, capable of real-time detecting and reporting to the Police of dangerous situations, such as traffic accidents and crimes, and also automatically identifying and tracking suspects and their vehicles related to incidents.
03
AI Installed in CCTVs
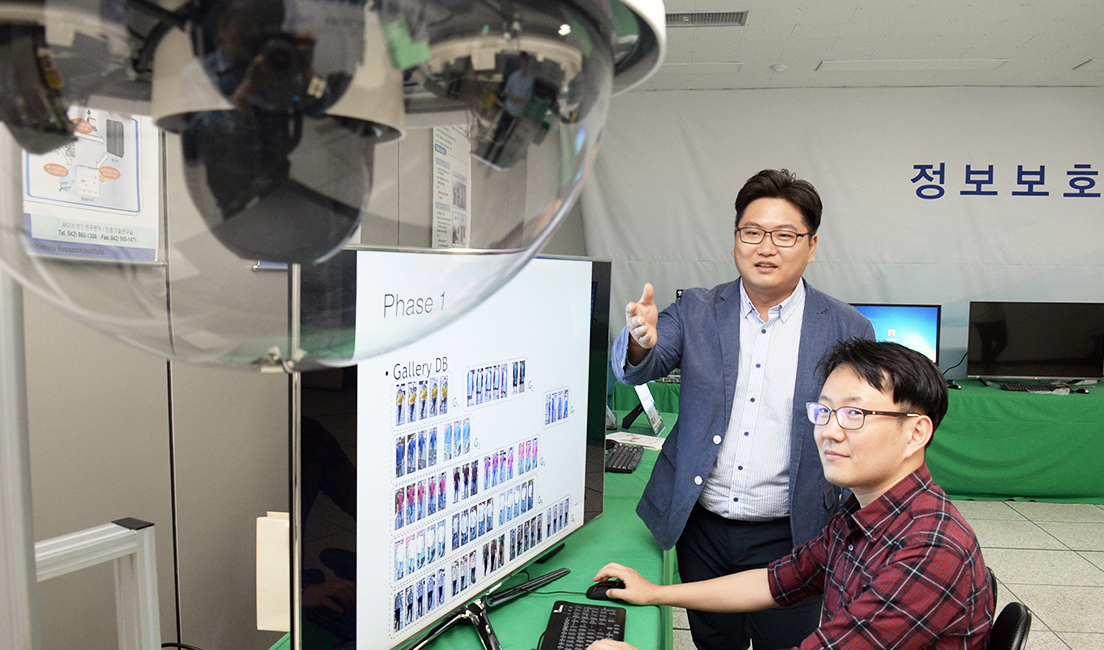
The development of computer-based technology capable of searching for missing children and preventing crimes and accidents without human involvement is gaining significant momentum. ETRI possesses various proprietary technologies that can be applied to such applications. Good examples are image deep-learning technology to detect traffic accidents, re-identification technology to identify and track suspects and their vehicles, big data learning technology of CCTV verification images, and technology to prevent image security infringement.
These proprietary technologies will help enable us to immediately detect crimes and accidents that occur during vulnerable time periods, e.g., at late night, and accurately identify and track dangerous situations that may arise. Also, in an attempt to overcome the limitations of human vision, research is underway to develop Deep Resolution, an intelligent license-plate recognition technology, which will later be applied to CCTVs for security purposes, thereby providing intelligence to the systems.
ETRI researchers expect that continuous technology development will enable CCTVs already in place to use AI technology to automatically extract vehicle information, such as vehicle type, color, and model name, and further to determine whether a detected vehicle corresponds to a criminal suspect on the loose. Also, HD CCTVs, collecting data at a rate of 30 frames per second, will make it possible to automatically detect and track dangerous security situations.
When applied to nationwide integrated CCTV control centers, Police Agencies, and electronic security companies, these intelligence technologies developed by ETRI will shift the overall security platform from reactive and treatment-focused to real-time response and prevention-focused, thereby actualizing a cutting-edge security platform for the future.
Geon-Woo Kim, a senior researcher at the Information Security Research Division of ETRI said, “We have achieved tangible research outcomes associated with security intelligence based on verification of security big data through R&D activities directly engaging entities who need and will eventually use these security technologies, such as Police Agencies and local governments. The application of these technologies as pilot projects will lay the groundwork for the future cutting-edge security platform and position us to lead the way in global trends of social safety technology.”
Now, what’s left for us to do is to figure out how we can use these new technologies properly. That is to say; the issue of privacy of persons appearing on CCTV images. Some people argue for this intelligent CCTV technology; others oppose it. In response, ETRI researchers are now focusing their efforts on areas where there is room for improvement, and thus approaching the final phase of its effort to make the world one step safer.